¶ Azure Sentinel
NOTE: a Level 400 Training on Azure is available
Azure Sentinel in a sentence: a cloud Native SIEM (a SaaS solution)
But, what does cloud native mean?
- Delivers instant value (no setup costs)
- Scales easely
- Uses AI and automation to improve effectiveness
¶ Collecting Events and create Visibility
¶ collecting logs
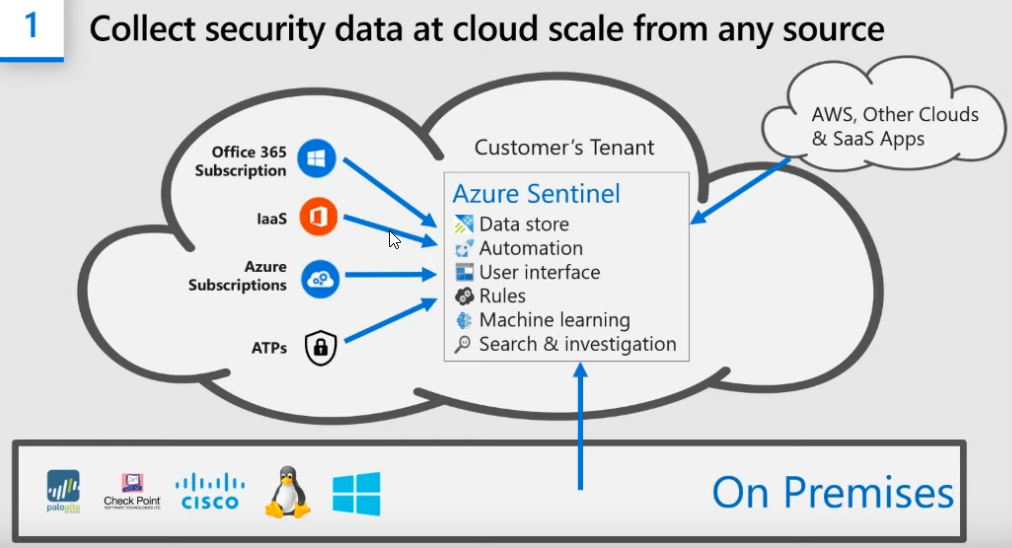
¶ Sentinel is able to collect Events from various sources:
¶ interesting Blog Posts:
-
Azure Sentinel: Syslog, CEF, Logstash and other 3rd party connectors grand list
-
Azure Sentinel: Collecting logs from Microsoft Services and Applications
-
Azure Sentinel Agent: Collecting telemetry from on-prem and IaaS servers
¶ collecting data from onprem:
- using Log Analytics Agent (for Windows; Linux)
- using Syslog (depends on SysLog Collector; LogStash or similar product)
- REST API (for partner products like F5; Barracuda; Symantec)
- custom connectors (Power Shell, Logic Apps; Azure Functions)
¶ Visualization
Built-in workbooks provide integrated data from your connected data sources to let you deep dive into the events generated in the collected data.
Using tempaltes you are able to build your own custom workbooks.
¶ Detecting / Analytics & Hunting
¶ how to detect threats
Sentinel allows you to detect threats using
- > 100 built-in analytics rules
- custom-created rules (using KQL queries)
- correlate events with threat intelligence and with URL intelligence
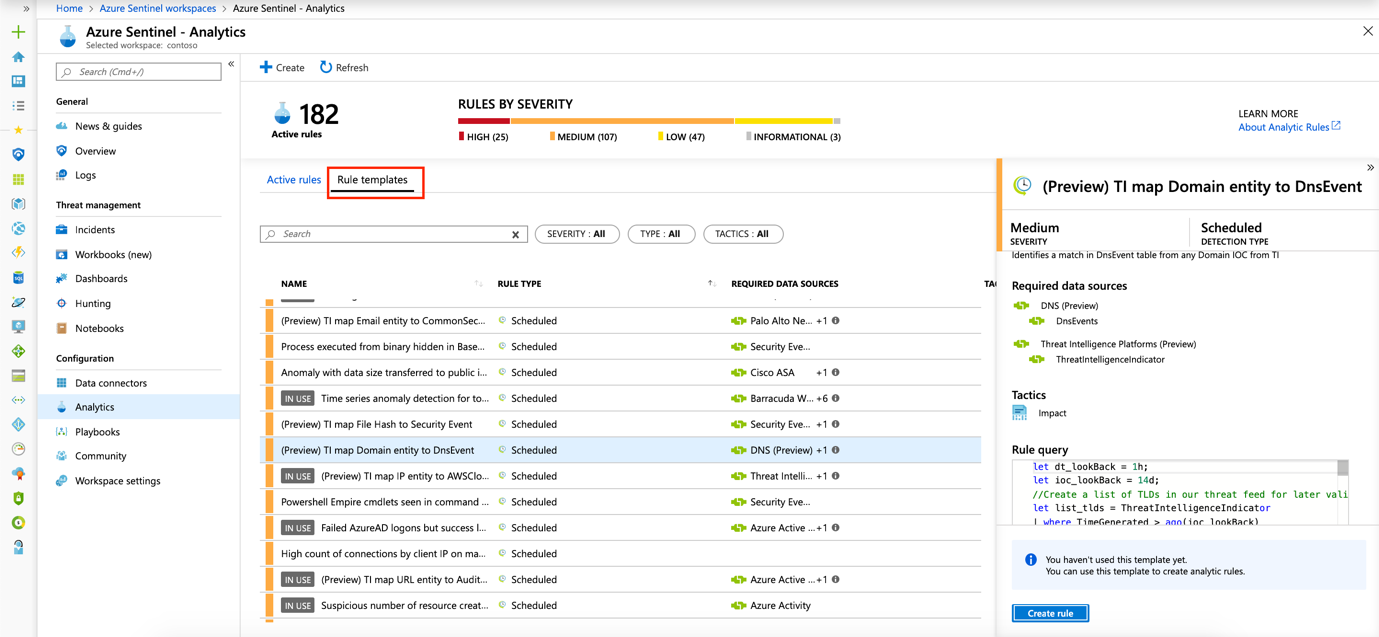
¶ Using Rules
After data sources are connected to Azure Sentinel, you want to be notified when something suspicious happens. This is where rules come into play. There are several rule templates available which were designed by Microsoft's team of security experts.
¶ Investigate and analyse Incidents
When a rule is triggered, an Incident gets generated. An incident is a collection of releted alerts, events and bookmarks.
Incidents can be forwarded / integrated to an existing ticketing systems (for example Service Now)
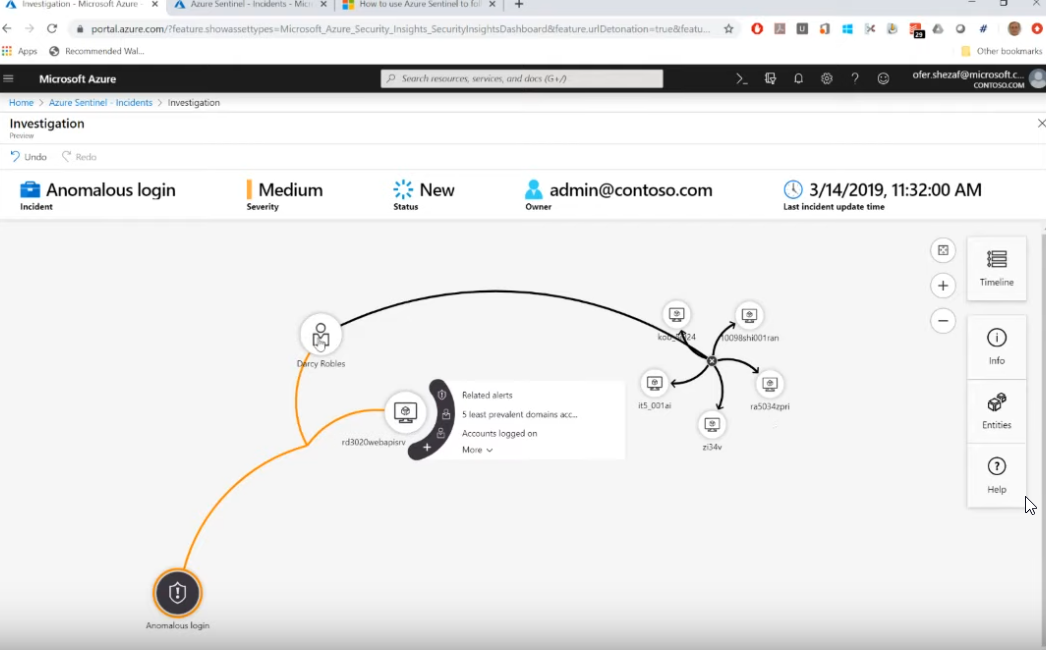
¶ Investigate
using the investigation GUI you can further investigate an Incident.
- Navigate the relationships between related alerts, bookmarks and entities
- expand the scope
- generate and view timelines
- gain deeper insight to related entities (user, domains, ...)